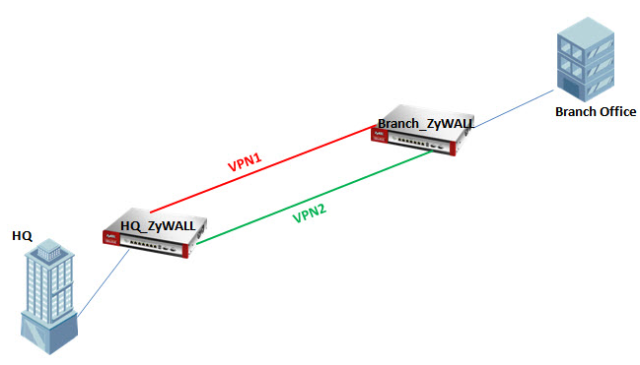
So another scenario, ZyXEL customer would like to load balanced and provide failover between their WAN links to route traffic for the VPN links having multiple links and VPN between two more sites using (ZyWALL USG’s) over VPN 1 and VPN2, so created a how to on this. Hope this helps.
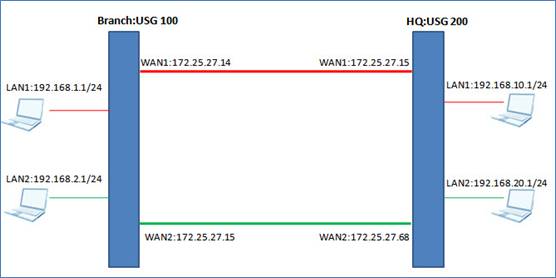
Topology
Requirements
· Traffic between USG100-LAN1 and USG200-LAN1 will go through VPN tunnel. (Red link)
· Traffic between USG100-LAN2 and USG200-LAN1 will go through leased link. (Green link)
· Achieve high availability in case any of the links goes down
Solution
In above topology, load balancing can be achieved. You can see traffic with different destination will route via different path.
Then we have to achieve high availability in case any of the links goes down.
Suggested configuration
VPN High availability on both WAN1 and WAN2 of USG 200.
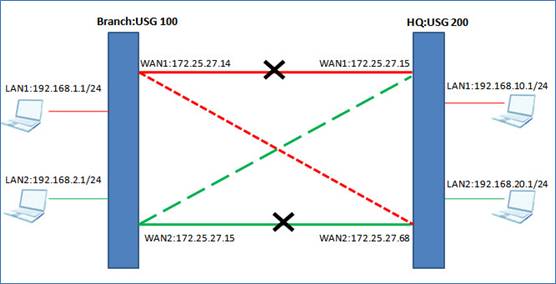
1. If USG200-WAN1 is down, USG100-WAN1 will try to build VPN tunnel to USG200-WAN2. So the traffic between USG100-LAN1 and USG200-LAN1 will go through VPN tunnel. (Red dashed link). This is VPN high availability
2. Once USG200-WAN1 goes up, USG100-WAN1 will still build VPN tunnel to USG 200-WAN1. This is VPN fail back. (Red link)
3. If USG200-WAN2 is down, USG100-WAN2 will try to build VPN tunnel to USG200-WAN1. So the traffic between USG100-LAN2 and USG200-LAN1 will go through the new VPN tunnel. (Green dashed link)
4. Once USG200-WAN2 goes up, USG100-WAN2 will still build VPN tunnel to USG200-WAN2. This is VPN fail back. (Green link).
Configuration Steps:
Part One: Configure the red link of the suggested topology.
On USG 100
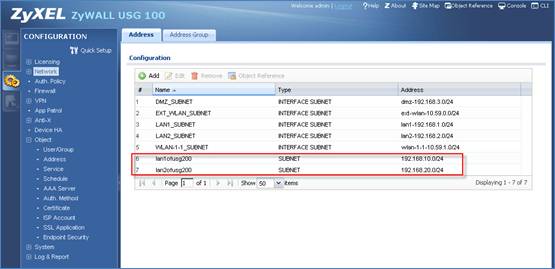
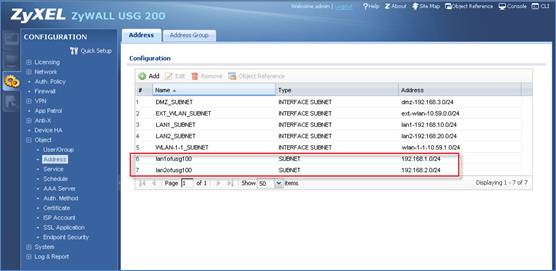
1. Add address objects for the LAN subnets of USG200.
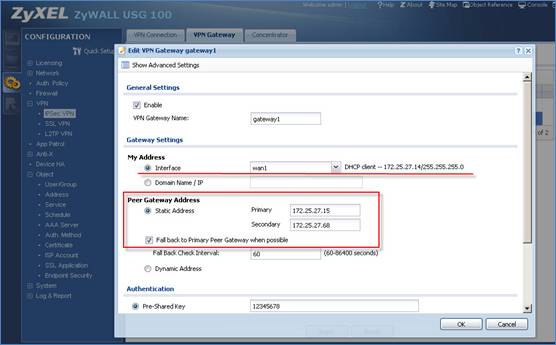
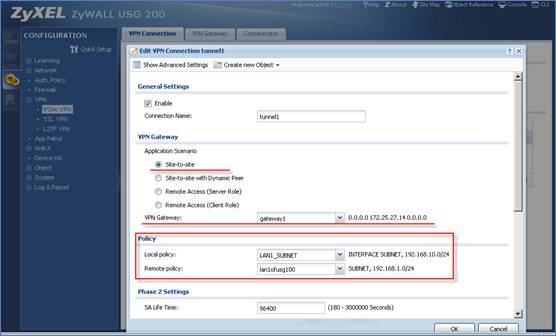
2. Configuring VPN gateway.
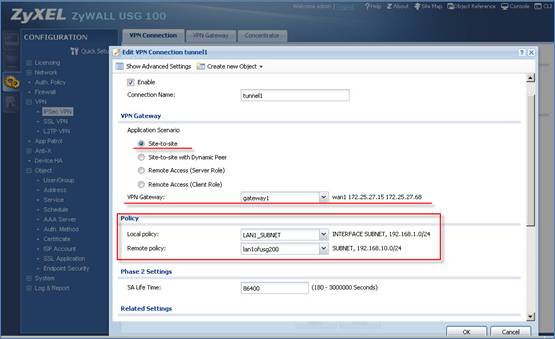
3. Configuring VPN connection.
Notice: In USG devices with 2.20 firmware, system will automatically create routes for VPN traffic according to VPN phases2 (VPN connection) local/ remote policy. Traffic whose source is in the local policy and destination is in the remote policy will be sent to the corresponding VPN tunnel. Thus there is no need to add policy route.
On USG 200:
1. Add address objects for the LAN subnets of USG100.
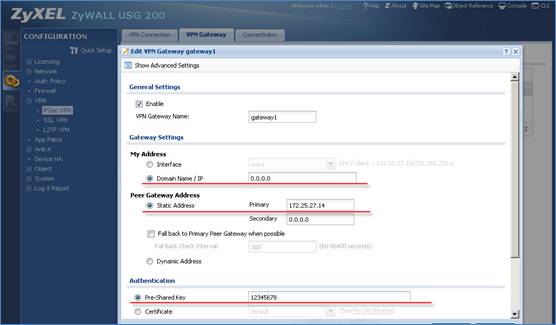
2. Configure VPN gateway.
3. Configure VPN connection.
Note : In USG devices running 2.20 firmware, system will automatically create routes for VPN traffic according to VPN phases2 (VPN connection) local/ remote policy. Traffic whose source is in the local policy and destination is in the remote policy will be sent to the corresponding VPN tunnel. Thus there is no need to add policy route.
About the configuration of the green link, you may refer to the above steps on both USG 100 and USG 200 , which will be the same …

bro can u give me ur contact no…..i want learn more from u
tq
Please feel free to post your questions to the blog, I will be more proactively updating my blogs.
I have a question from ports. In my configuration “ZyWALL IPSec VPN failover and loadbalancing using ZyWALL USG Devices” when the connection goes down on link1 the time needed to create the connection on link2 VPN1 is about 30 seconds, it loses a dozen ping. And ‘this behavior normal or is it possible to optimize it?
Hi Lorenzo, if you have set the failover settings to 30 seconds, the USG will wait 30 seconds before switching to the second (stand by) connection, if you prefer to decease that time window please note that although your standby connection would be activated much quicker and you wouldn’t lose much traffic (including ICMP) but this can also falsely trigger a tunnel switch over, especially if your primary WAN connection has intermittent connectivity issues.
Let me know if you have further issues.
My Endpoint devices are Zyxel usg300 and Zywall35. I have 2 links for both active WRR Configuration Active / Active Weight 1.2. Connections are monitored with ping http://www.google.it Timeout 1s and 5s with Tolerance Period 2, while VPNs are monitored on ZyWALL 35 with standard parameters while on Usg300 is monitored with the following parameters Tolerance1 1s Timeout Period 5s. Do you think I can improve and get to lose at most a couple of packets in the switch from port 1 to port 2?
I wouldn’t suggest decreasing the timeout values any lower than that, beside you have already lowered the values to their minimum capacity. You may want to change some of the IPSEC VPN parameters if the tunnel is taking too long to establish.
Thank you Adeel for your detailed demo regarding VPN failover. I have a few questions.
I have two ZyWall USG 100s on two different sites. I want to achieve both WAN and VPN failover. I followed your demo quite easily. However, I want to understand your settings on USG 200. The settings on usg 100 are straightforward, however, you made a change in the pattern of usg 200 settings. That is, under vpn gateway, you used zeros (0.0.0.0) for “My Address” and used a single gateway ip address (primary only) for “Peer Gateway Address”. What’s the reason for this to be different than than the settings on usg 100? I used the exact same settings of usg 100 on both firewalls for testing and it didn’t work until I removed the gateway attachment to the 2nd WAN link. I had created each gateway separately to on both WAN connections, thinking if one is not available, the other should pickup, but again. that didn’t work.
Secondly, where do you setup the wait time before the tunnel fails over? and are there any suggestions for WAN failover? for basic internet use, other than the vpn failover off course.
Thank you very much for your kind response.
Hi Hanif
The (0.0.0.0) for “My Address” means that your IPSEC tunnel can be sourced from any address, we need that for the fail over purposes as if we specify one address the tunnel would not build from the second (Backup) WAN address. You can use “0.0.0.0” on both endpoints if you want a fail over to work both ways and on Both WAN gateways.
The tunnel fail over settings should be in phase 1, but this may vary depending on the firmware you’re using. The WAN failver timers and in WAN settings under interfaces. You may keep the timers to he lowest values for faster switch overs if you have a stable connection, as this can cause false positives if you have an high latency or low bandwidth connection.
HTH
Excellent!!! Thank you very much Adeel. It’s very clear now. I have now tested your recommendations and it went smooth. 🙂
Have you ever considered about including a little bit more than just your articles?
I mean, what you say is fundamental and everything. However just
imagine if you added some great graphics or videos to give your posts more, “pop”!
Your content is excellent but with pics and videos, this site could undeniably
be one of the best in its field. Wonderful blog!
Have you ever considered writing an ebook or guest authoring
on other sites? I have a blog centered on the same information you discuss and would love to
have you share some stories/information. I know my viewers would appreciate your work.
If you are even remotely interested, feel free to shoot me an e-mail.
For most recent information you have to go to see the web and on web I found this website as a finest site for most recent updates.
Hello, I think your website might be having browser compatibility issues.
When I look at your blog in Firefox, it looks fine but when opening
in Internet Explorer, it has some overlapping.
I just wanted to give you a quick heads up!
Other then that, terrific blog!
I blog frequently and I really appreciate your information.
This great article has really peaked my interest. I will bookmark
your site and keep checking for new information about once per week.
I opted in for your RSS feed as well.
Hi! I’m at work browsing your blog from my new iphone! Just wanted to say I love reading your blog and look forward to all your posts! Keep up the superb work!
I have a problem slightly different from this cool setup.
At the branch office I have an USG110 and at the main office I have two USG200 (one controls the general access to network resources and the other one telephony, each has their own public IP). I need to connect to both USG200 firewalls from the USG100 but can’t seem to make it work, any suggestions?
Questions.
1.should the local network have two different subnet?
2. what if i have only one single local network in both end would it be possible?
3. should i create additional tunnel or just a secondary ip in peer gateway?
I hope that someone is still reading this blog entry. I will be setting up a network that will have multiple VPN connections. The secondary locations will not have internet failover but the primary location will. When setting up my scenario will the remote office use the VPN gateway with it own WAN_1 interface or will they also require the 0.0.0.0 for the local Phase1 build?
I am genuinely pleased to read this weblog posts which consists of tons of
helpful facts, thanks for providing these kinds of statistics.
can you assist me sir regarding my usg 300 and usg 20 vpn tunneling?